As I wrote in a previous article Microsoft is adding more and more settings that are supported to be managed with Microsoft Intune. Two of these settings are available with the release of the Windows Insider build 20226;
DisableCMD and DisableRegedit.
With these two settings, we are able to block access to the Command Prompt and Registry Editor on Windows devices using Microsoft Intune.
As I wrote in the previous article, to control these new settings we need to use a Custom configuration profile in Intune. If you are not familiar with these kind of profiles, please read my previous post first.
The settings were already supported in build 20175 but Rudy Ooms and I found a bug related to these settings. After reporting this to Microsoft the bug which is fixed in the latest build.
Create custom configuration profile
Let`s create the custom configuration profile to block access to the CMD and regedit.
- Sign-in to the Endpoint Manager admin center
- Browse to Devices – Windows
- Browse to Configuration profiles
- Click +Create profile
- Choose Windows 10 and later as Platform
- Choose Custom as Profile
- Click Create
- Give the profile a Name
- Enter a Description (Optional)
- Click Next
- Click Add on the Configuration settings tab
- Give the Row a Name
- Fill in the OMA-URI: ./user/vendor/MSFT/Policy/Config/ADMX_ShellCommandpromptRegeditTools/DisableRegedit
- Data type: String
- Value:
<enabled/>
<data id="DisableRegeditMode" value="2"/>- Click Save
- Click Add
- Give the Row a Name
- Fill in the OMA-URI: ./user/vendor/MSFT/Policy/Config/ADMX_ShellCommandpromptRegeditTools/DisableCMD
- Data type: String
- Value:
<enabled/>
<data id="DisableCMDScripts" value="1"/>- Click Add
The two settings are added to the profile, finish creating the profile by assigning the profile to a security group.
End-user experience
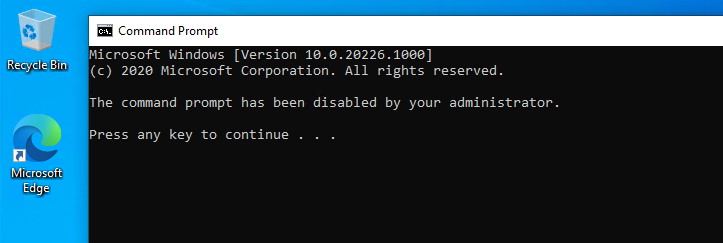
We can be short about the end-user experience.
Access to the Command Prompt is blocked.
And also access to the Registry Editor is blocked.
This still allows access to both by running it as administrator.
Thank you for reading.

12 Comments
I like both of these settings and will enable then via Intune as soon as they are available. Great article!
Hi Peter Nice Blog
Small query, if i block command prompt this way, will the Batch files deployed via INTUNE will also be blocked ?
I read the full CSP of this new feature and i can see you can also block apps and the question is if i block powershell with this new CSP, will the powershell Win32 apps and script deployed via INTUNE will also be blocked ?
It should behave the same as using a GPO to block CMD. It should not block such a script.
Will this work on Windows 10 Education? Not having much log deploying it.
Hello, this is not applicable on Windows 10 enterprise version 2004 build 19041.546? I get the message below in Intune.
ERROR CODE
0x87d1fde8
ERROR DETAILS
Remediation failed
No this isn`t supported on 2004, the minimum Insider build is mentioned in the port.
i am getting error for windows 10 enterprise version 1909-18363.1198. OS version does not support this configuration?
That`s correct. The article starts with info what the minimum Windows build is on which it`s supported; Insider build 20226. 1909 is not supported.
I there a way to make this work if I have a local account in Windows, that was created by Intune? The local account is a standard user, not and administrative user, and I wanting to disable the CMD Prompt, Reg Edit and GPEDIT and I have tried other OMA-URI’s like the two below, and can not get them to work in Windows 10 Educational Pro 20H2.
./Vendor/MSFT/Policy/Config/LocalPoliciesSecurityOptions
./user/vendor/MSFT/Policy/Config/ADMX_ShellCommandpromptRegeditTools
Do I need to change the ./user/vendor to be ./user/Correct Account Name?
can you do the same for powershell? will it stop intune running sdcripts
I also want to know if you can do it for Powershell. Thanks
The settings are applied successfully to a device group in Intune but now even me as admin can`t open it. When I use open/run as admin option it just gives me same msg that it`s disabled by Admin and same case is with Regedit.