Since the first day Microsoft released Windows 10 there is a lot to do about the data Microsoft is collecting from you when using this OS. A lot of those apps connect to the internet and you have no idea what data is collected
In this blog I will show you how you can use Microsoft Intune to take control of the privacy settings on the company managed devices.
Setting up Intune policies
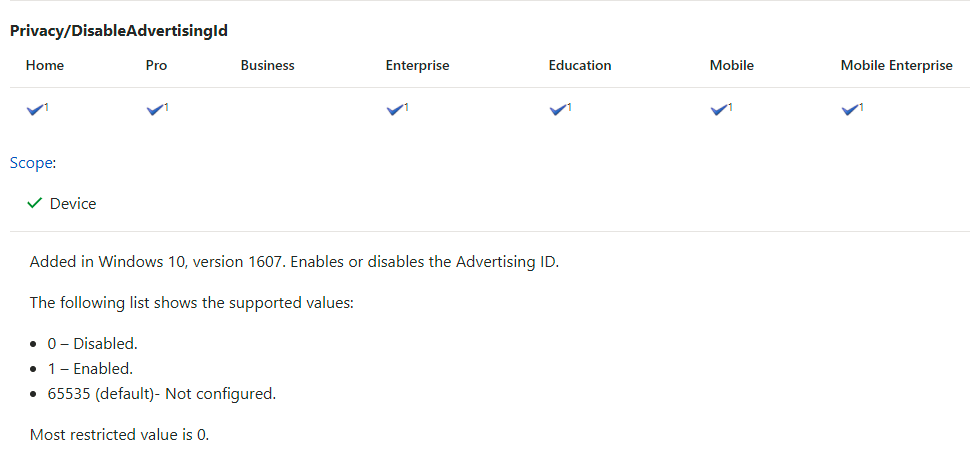
To block apps from accessing you information with Microsoft Intune we need to use CSP policies which you can find on docs.microsoft.com. We will first disable the Advertising ID. Look up for the right policy under Privacy. On the below screen you see Privacy/DisableAdvertisingId, this is part of the OMA-URI you need to set in the Intune configuration Profile. And you can see there are three options which you can set by providing one of the three corresponding numbers in the Intune policy.
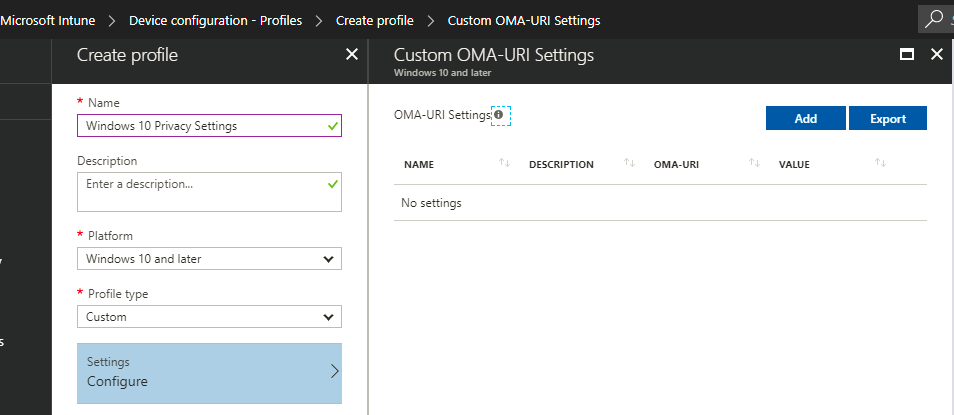
Now open the Azure portal and open the Intune tab. Choose Device configuration, Profiles and click on Create profile.
Give the policy your preferred name, choose Windows 10 and later as platform en policy type is Custom. Next to OMA-URI settings click Add.
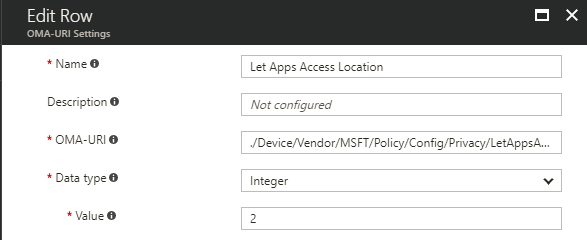
Give the Row a name, as OMA-URI you see a complete OMA-URI (part of that we found on docs.microsoft.com), Data type is Integer and add the value 1 to Enable the setting.
OMA-URI: ./Device/Vendor/MSFT/Policy/Config/Privacy/DisableAdvertisingID
Data type: Integer
Value: 1

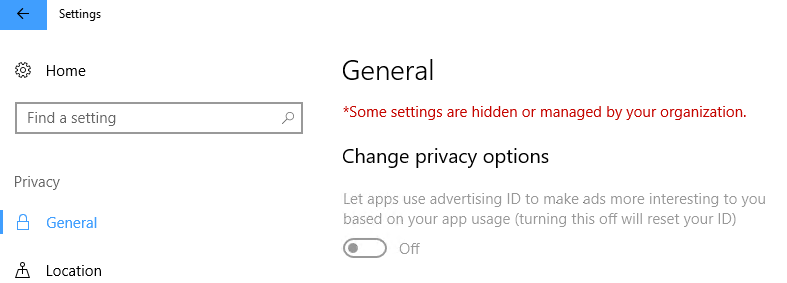
Now perform a sync with Intune on a managed Windows 10 device and switch over to Settings, Privacy, General. Let apps use advertising is switched off and greyed out. You also see a message some settings are managed by your organization.
The next example is to block apps from accessing your location. On docs.microsoft.com you can find the policy and options you can set.
 Add an extra Row in your Intune policy and use these settings:
Add an extra Row in your Intune policy and use these settings:
OMA-URI: ./Device/Vendor/MSFT/Policy/Config/Privacy/LetAppsAccessLocation
Data type: Integer
Value: 2
After syncing the setting from Intune, switch over to Location. Location service is switched off and greyed out.

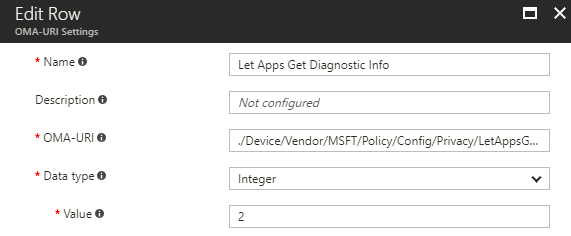
The third example is to stop apps from accessing the diagnostics information. Look up the policy we need for this; Privacy/LetAppsGetDiagnosticsInfo

Add an extra Row in your Intune policy and use these settings:
OMA-URI: ./Device/Vendor/MSFT/Policy/Config/Privacy/LetAppsGetDiagnosticsInfo
Data type: Integer
Value: 2
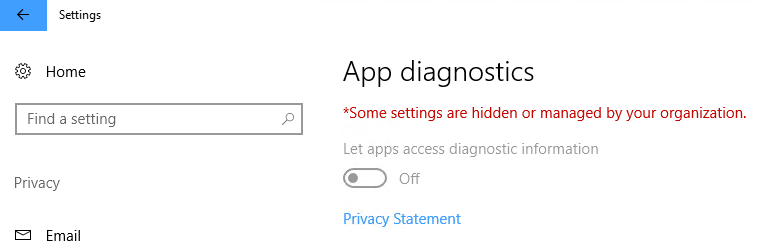
Perform a sync again and this is the result for Diagnostics.
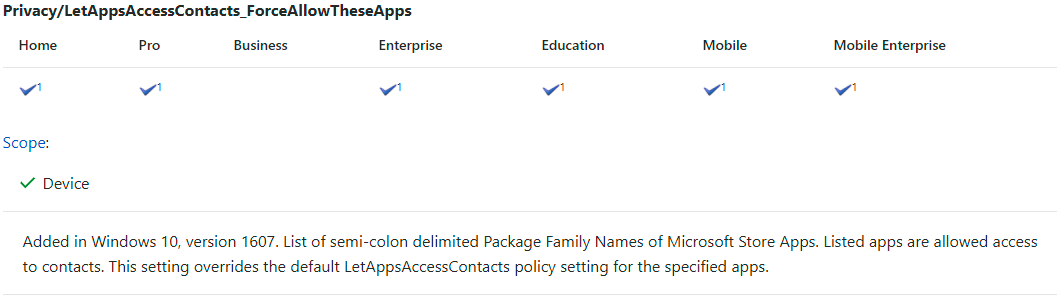
With these examples you are able to completely turn these privacy settings on or off. There are also policies to force allow or force deny an specific app access for example your Contacts. To Deny apps access to contacts you need to provide these apps Package Family Names, semi-colon separated.
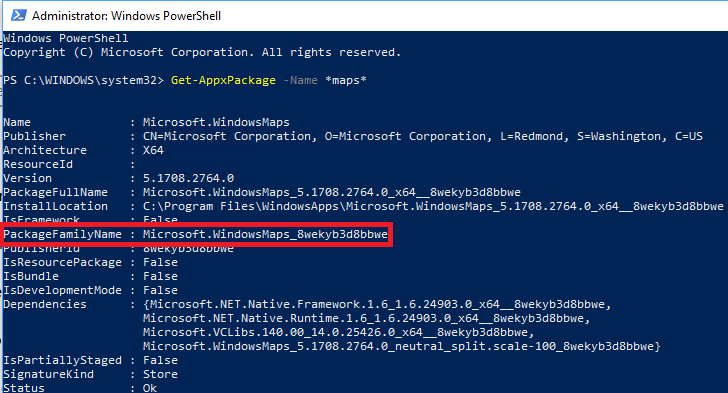
To get the Package Family Name for the Maps app, open PowerShell Get-AppxPackage -Name *maps*
Use the PackageFamilyName in your Intune policy.
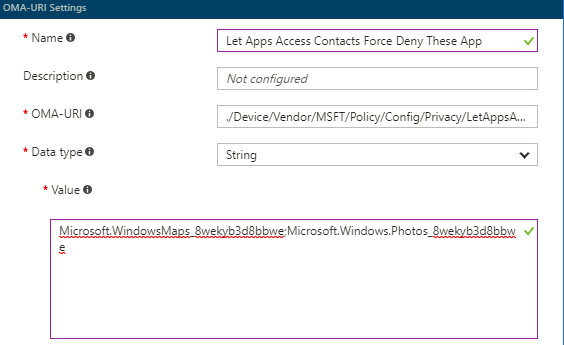
OMA-URI: ./Device/Vendor/MSFT/Policy/Config/Privacy/LetAppsAccessContacts_ForceDenyTheseApps
Data type: String
Value: Microsoft.WindowsMaps_8wekyb3d8bbwe;Microsoft.Windows.Photos_8wekyb3d8bbwe
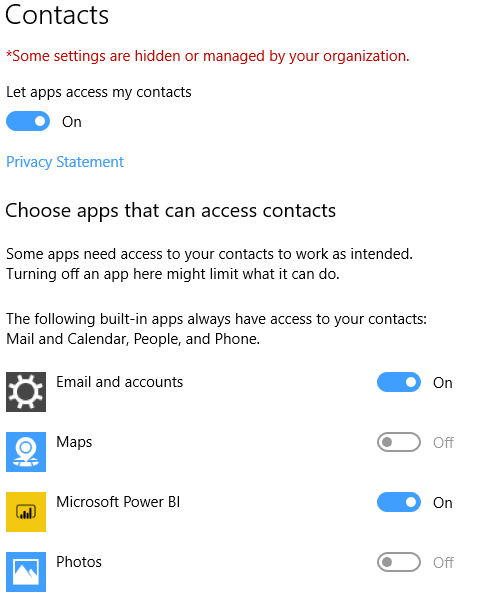
When we now go to the Contacts tab you see the overall setting is not greyed out. The two apps are force denied, all other apps can be turn on/ off by the user.
With these examples you should be able to take control over most of the Windows 10 privacy settings using Microsoft Intune.
Update November 17th:
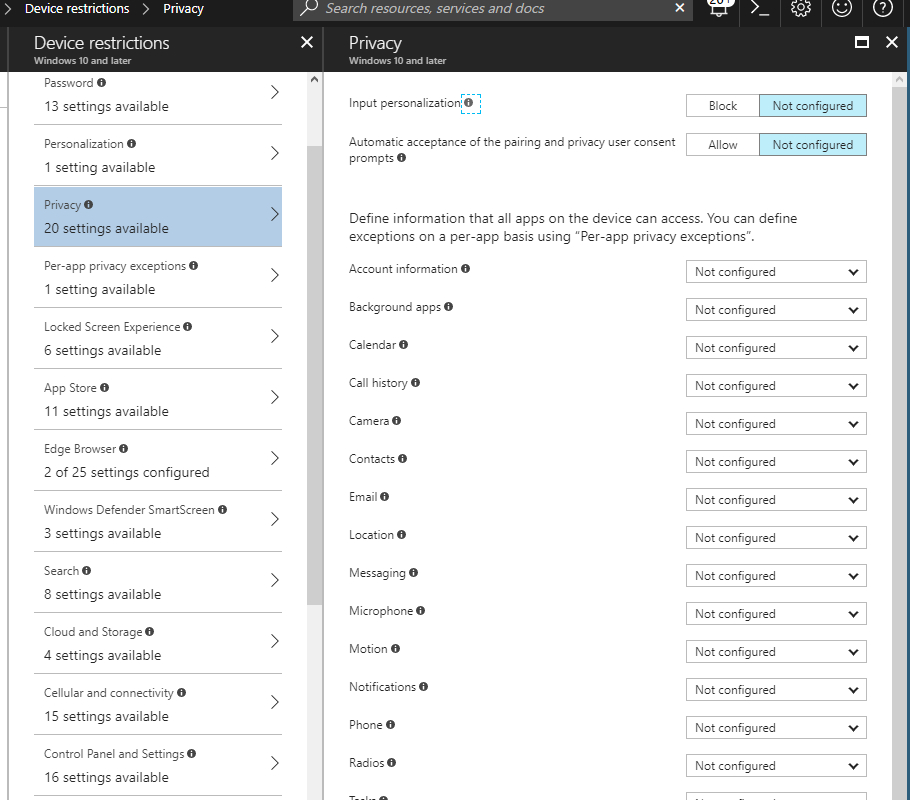
Today I was setting up a Windows 10 configuration policy for one of our customers and I noticed two tabs under Device Restrictions one called Privacy and the other one Per-app privacy exceptions. I really have no idea since when these tabs are there, maybe they are completely new, maybe I just haven`t noticed them for weeks, but this makes life much easier when setting Windows 10 Privacy settings :).
Below you can see almost all the privacy settings discussed before in this blog. On this tab you can set an Allow or Block for the mentioned app.
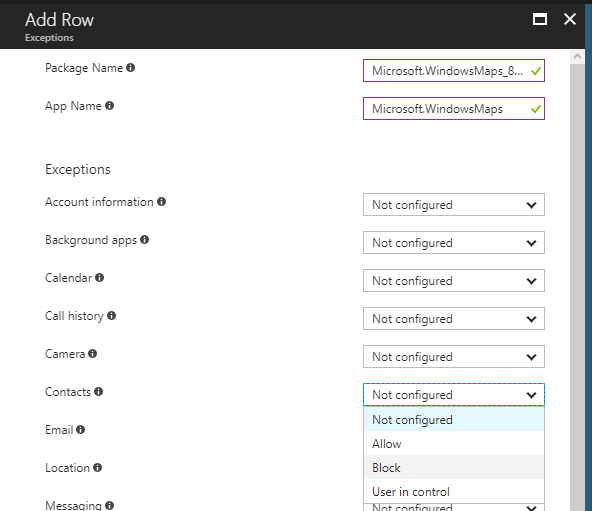
When we open the second tab we can add separate apps by row and we can set an exception for every app.
Again we need the Package Family Name you can query with PowerShell and the App name. Then you can choose per app if you want to Allow or Block the app, or Leave the user in control.

![Control Windows 10 privacy settings with Intune [UPDATED]](https://inthecloud247.com/wp-content/uploads/2017/11/01a-Choose-privacy-settings-for-your-device.jpg)
1 Comment
You have LetAppsGetDiagnosticsInfo rather than LetAppsGetDiagnosticInfo