
We are managing Windows 10 clients with Microsoft Intune as MDM devices. This provides us the option to deploy software (.msi files) to these Intune managed devices. Today we have a look at deploying Heimdal Security, which we use to increase security on our devices on which Windows Defender Anti-virus is also active.
Editing the Heimdal msi file
The first thing we need to do to be able to deploy Heimdal with Intune is editing de msi installer file to include the serial key. You can use Orca to edit the installer file which is part of the Windows SDK Components for Windows Installer Developers, more info and the download link can be found here.
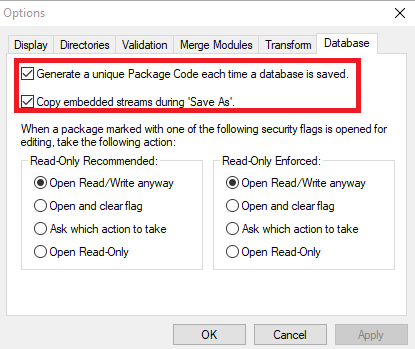
Open Orca, in the menu go to Tools, Options. On the tab Database make sure you check the first two options and click OK.
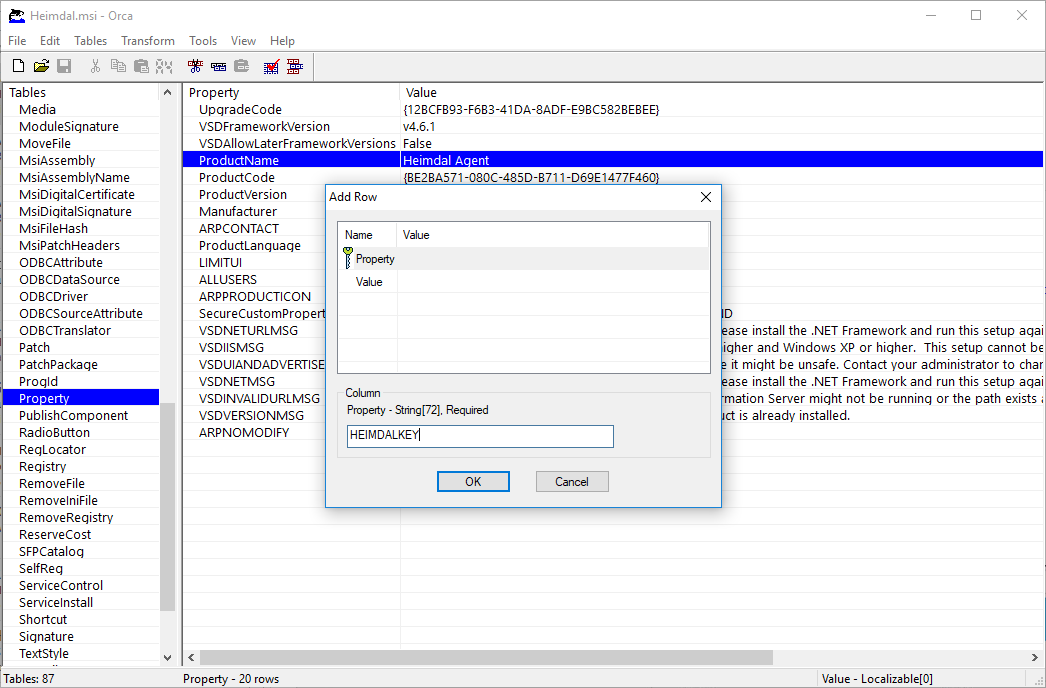
Now download your msi installer file from the Heimdal Unified Threat Dashboard and open the file in Orca. Scroll down to the table Property, from the menu choose Tables and Add Row.
In the property field write HEIMDALKEY
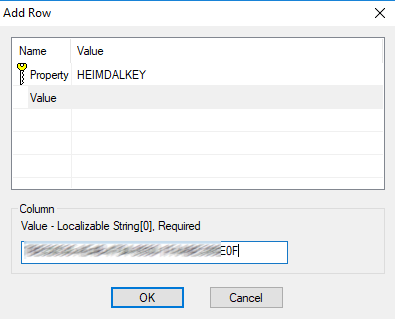
In the value field write your serial key. Your serial key is the Heimdal Corp Activation Key which can be found in the dashboard. Click OK.
You see an row with HEIMDALKEY and your serial like below.
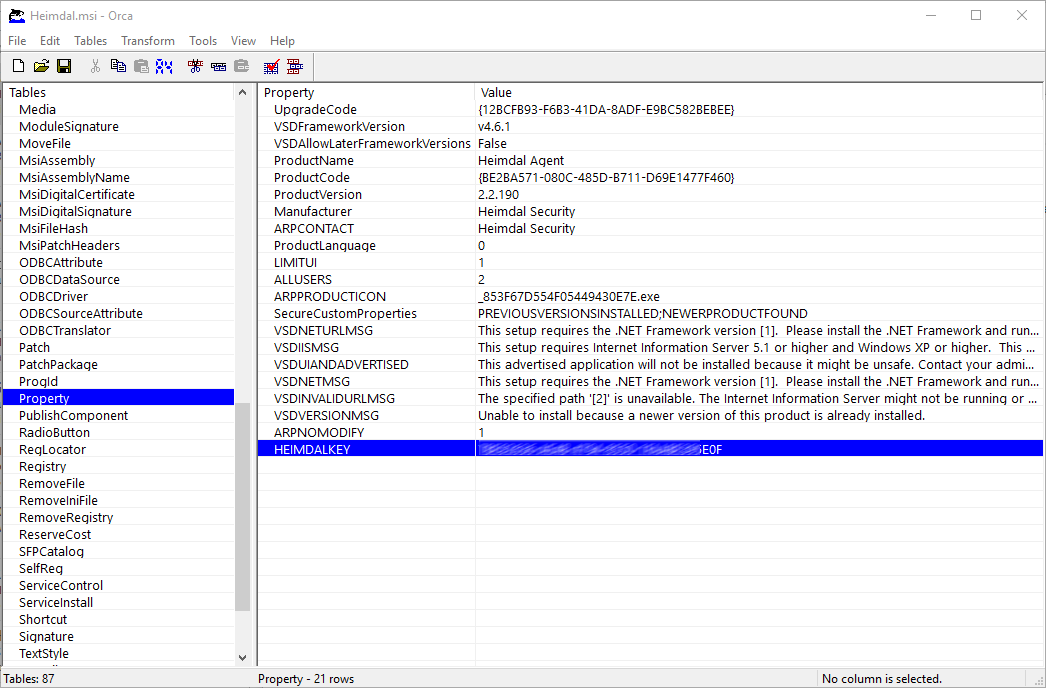
Save the file on your computer. The file is ready for deployment.
Deploy the Heimdal msi file with Microsoft Intune
Logon to the Azure portal and open the Intune tab. Click on Mobile apps, Apps and Add to add a new application to deploy.
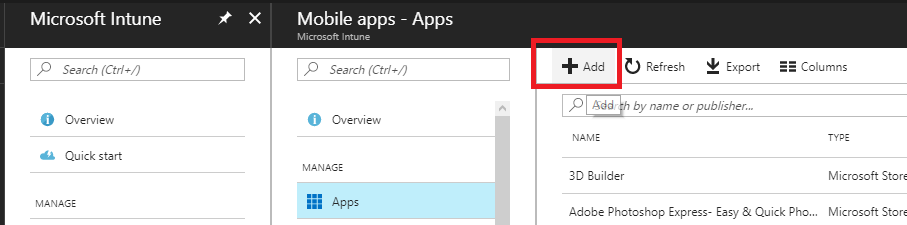
As App type choose Line-of-business app.
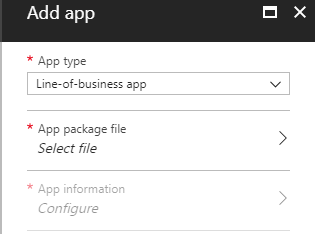
Click on Select file and browse to your self created Heimdal msi file and click OK.
Click on Configure. Add the required information about the application (Name, Description and Publisher). We don`t need to add a Command-line argument.
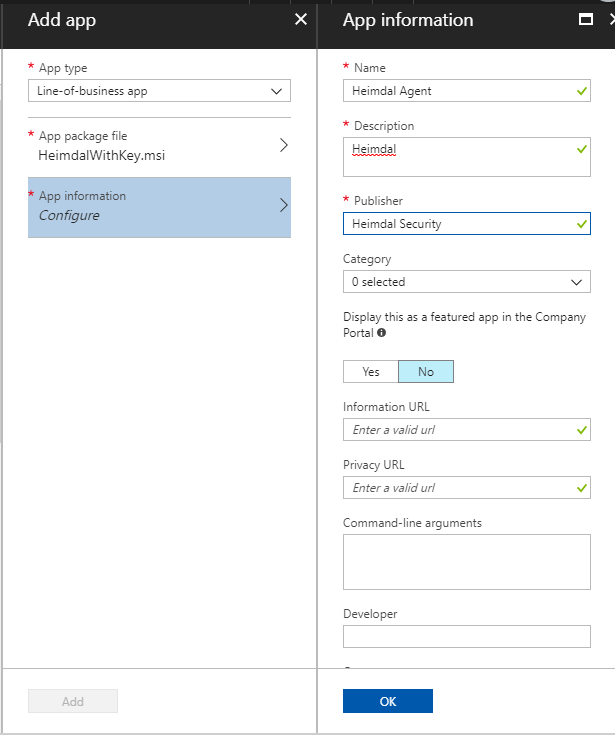
Click on Select image to upload the Heimdal logo. Browse to an image file with the Heimdal logo and click OK and Add.

After uploading the installer file click on Assignments. Pick a group to assign the deployment to and the assignment type. I took a device group and deployment type Required. When you choose required the installation will be forced to install. When yo choose Available, the user is able to install the application from the Intune Company portal.

Heimdal installation
When a device sync is done Intune is triggered to install Heimdal to the users device when the assignment type is Required. No action is required from the user.
If you choose Available as assignment type, your user needs to open the Intune Company portal to install Heimdal. Click on the app icon and choose install
After installation on to the Windows 10 device, in the taskbar you see the Heimdal icon which confirms the successful installation of Heimdal. To confirm the correct license is applied, which we added to the installer file, open Heimdal and open the license tab. You notice the last few numbers/ letters from your license key.

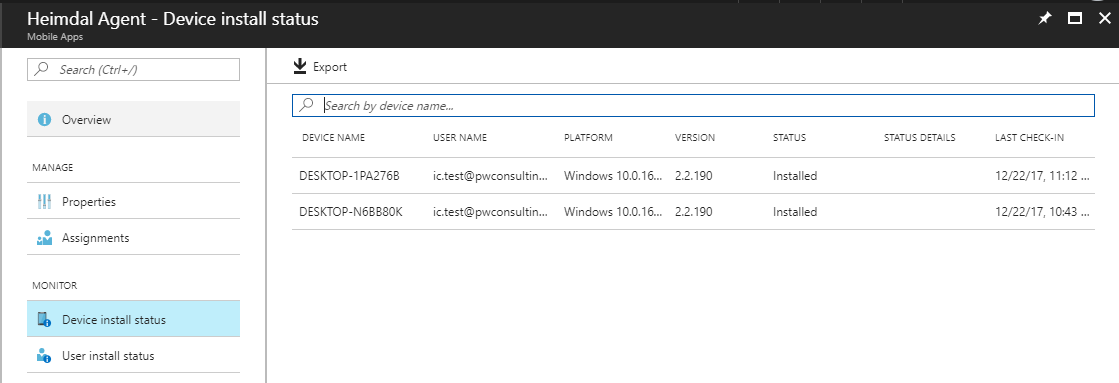
In the Intune portal you open the Heimdal app and click on Device install status. After a short period your devices show up with a install status.
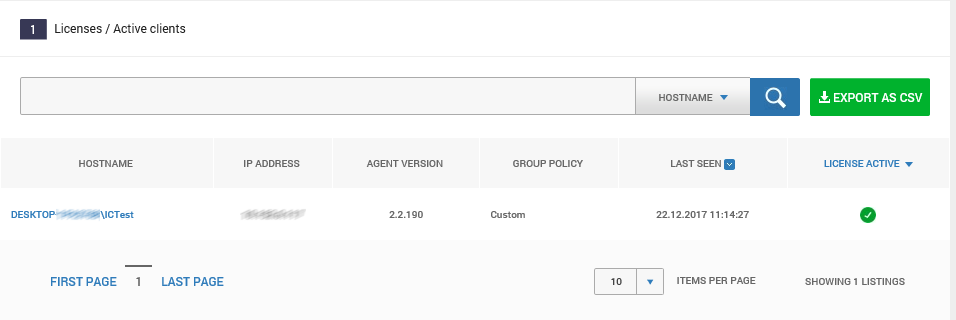
And as last, from the Heimdal Unified Threat Dashboard you see the devices show up activated.

Be the first to comment