Today a short article on configuring FIDO2 security keys as the default login option for your Windows devices. I describe how we assign the default credential provider with Microsoft Intune, which is the logon setting to configure the FIDO Credential Provider as the credential provider.
Besides configuring the default credential provider, we can also exclude credential providers, to remove login options from the Windows logon screen. We can use this setting to block for example the usage of a password.
The combination of setting the default configuration provider to security keys and removing the password as a credential provider might come too early for default Windows end-user devices, as this also affects for example RDP and remote support (which also can’t use passwords). But for shared multi-user desktops or kiosk devices (where end-users sign in with their (Azure) AD account), these things should be less of a problem. Sign-in with a FIDO2 key to such multi-user devices is very easy for the end-user and very safe.
Credential Providers
To configure credential providers, we first need to find the corresponding GUID/ CLSID of the credential providers. The easiest manner to find the GUID we need is to check the registry of a Windows 10/11 device.
A list of registered credential providers and their GUIDs can be found in the registry at HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Authentication\Credential Providers.
All these GUIDs correspond to a credential provider. A few well-known credential providers are:
| PasswordProvider | {60b78e88-ead8-445c-9cfd-0b87f74ea6cd} |
| FIDO Credential Provider | {F8A1793B-7873-4046-B2A7-1F318747F427} |
| Smartcard Credential Provider | {8FD7E19C-3BF7-489B-A72C-846AB3678C96} |
Configure the Credential Providers
We can configure the credential providers with a GPO, but I only show how it is done using Microsoft Intune. The setting is, like thousands of other settings, available in the Settings Catalog profile.
Let’s sign into the Intune portal.
- Browse to Devices, Windows, Configuration profile
- Click Create profile
- Select Windows 10 and later as Platform
- Select Settings Catalog as Profile type
- Click Create
- Enter a Name for the profile
- Enter a Description (optional)
- Click Next
- Click Add settings
- Open Administrative Templates, System, Logon
- Select Assign a default Credential provider
- Select Exclude credential providers (Optional)
On the left, the settings we selected are available to configure.
- Switch Assign a default credential provider to Enabled
- Add {F8A1793B-7873-4046-B2A7-1F318747F427} as the Default credential provider.
If you also want to exclude (remove) credential providers, add the GUIDs from the corresponding credential providers to Exclude the following credential providers.
- Switch Exclude the following credential provider to Enabled
- Add the GUIDs from the corresponding credential providers
In case you want to exclude multiple credential providers, separate the GUIDs with a comma.
Finish the creation of the profile by clicking Next and assign the profile to a security group.
The end result
After the policy settings are applied, the device first needs a restart before the settings are active.
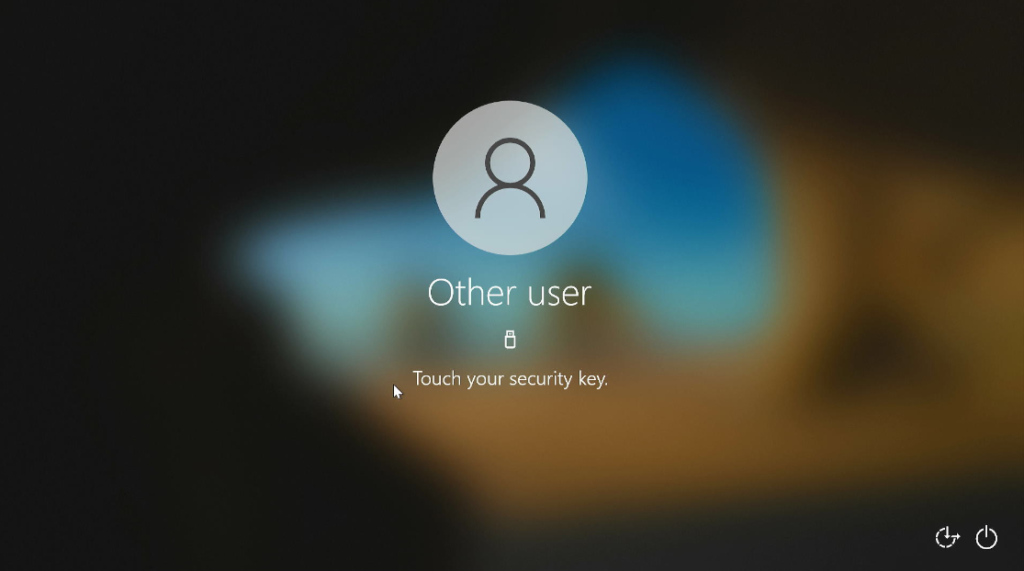
But after the restart we immediately see on the sign-in screen, security keys are set as the default sign-in option, even as the key is not yet inserted into the device.
With a FIDO2 (bio version) security key inserted, it asks to touch the key.
When we only set the default credential provider to FIDO Credential Provider but did not exclude other credential providers, we still have to Sign-in options shown on the screen. In this case, I have the options password and smartcard also available to sign in to my kiosk device.
But after excluding these two credential providers, the Sign-in options are removed and I can only sign in to my device with a security key.
I used a biometric version FIDO2 key, which has fingerprint recognition. To sign in to my device, I insert the key and only touch the key once with my finger to get signed in to the device.
This is a very user-friendly sign-in option to use for multi-user-like devices.
if you are interested in taking the next step in going passwordless, I suggest to also read this blog post.
Thanks for reading!

19 Comments
Can you tell us exactly which FIDO key you used to achieve this?
Especially since you describe that the FIDO key is also used for your fingerprint.
I myself have a yubikey and as far as I know it has no fingerprint recognition.
Good post by the way. Does setting this default login method also mean that the windows hello PIN code is no longer an option or does it remain on as an option in addition to logging in via the Fido key?
I have blocked Windows Hello on this device to avoid users need to go through the WH registration. But setting a default credential provider doesn’t block other credential providers.
For this setup I used a Feitian K27 key.
Thanks for your reaction Peter, that answers my questions so far.
Do you also know if it is possible with this solution to have the device locked when the Fido key is ejected, like with a smartcard solution?
There is no policy or something related to get this done.
So, that would mean creating something yourself which get triggered by removing the key.
Thanks Peter,
I have the Fido authentication working, set as default and disabled all the other credential providers.
Working fine so far.
I will try to find a solution for triggering a lock when removing the key from the device.
Hi Peter,
Do you know if it’s possible to exclude multiple credential providers for this? If so, how are the two exclusions separated?
Thanks in advance!
Hi Koen,
I totally forgot to mention how to exclude multiple credential providers. Separate the GUIDs with a comma should do the job.
Awesome! Thanks for your quick response Peter, this seems to work just fine!
Just one more questions Peter, when adding multiple credential providers, and separating them with a comma, do I have to use space after the comma or only comma and then next provider tag?
Thanks!
Just a comma, no other spaces.
windows hello for business and FIDO both are phishing resistant have similar security.
just thinking why any org will invest in FIDO if they have WHFB.
To setup WHfB, you still first have to sign in to the device with a password, that’s where the FIDO key comes in.
And on shared Windows devices sign in with a sec key is preferred above sign in with a password.
Hi Peter, one last question. When WHfB is forced, it seems that after adding and deploying this policy, the setup PIN (set up by WHfB) is still usable for login. Do you know if it’s required to turn off this WHfB, so that PIN code is no longer usable?
Or am I using the wrong GUID of the PIN credential provider? If yes, do you know which one I should use?
Thanks, again!
Thanks for this article Peter! I’ve just tried to set this up using a FIDO2 key and am asked to set up and then use a PIN with the key.
So at the Win login screen with the USB inserted it asks first for a PIN and then to touch the security key (might as well just use Win Hello PIN with this workflow).
Have MS changed this requirement since you published this article?
I want to be able to log in to windows by just touching the security key as in your article. I’m using a Thetis key which is U2F & FIDO2 (but doesn’t have a fingerprint reader like your key).
Hi Mike,
You are asked for a PIN because you are not using a BIO version key with a fingerprint. If you would have such a version, you’re not asked for a PIN.
Hi Peter,
first of all thanks for this tutorial. Question from our side would be, if it is still possible to use Password Authentication for UAC prompts and Admin Login.
We would like to have our users forced to use the FIDO 2 Stick, in our case YubiKey 5, but the UAC prompt would still need a password and it must be possible to login as Admin using a password.
Looking forward for your thoughts 🙂
Hi Richard,
What is described in this article is only related to the sign-in options you have on the logon screen. You can still authenticate inside Windows itself with a password.
That’s different if you take the next step in going passwordless as you can read in this article https://inthecloud247.com/the-next-step-in-a-passwordless-windows-experience/
guided me well but found that windows 11 turned round and said shows smart card requires drivers that are not present on this system W11 – I got in touch with the key provider and they led me down the line of reg key
REG ADD “HKLM\SOFTWARE\policies\Microsoft\FIDO” /v EnableFIDODeviceLogon /t REG_DWORD /d 1 /f
for some reason despite me putting the FIDO as credential providor it didn’t like the fido 2.1 nfc card in the reader, once I used that reg key it worked fine but still showed smartcard as an option instead. I’m sure it’s so simple if look deeper into it but up and running at the moment. So just providing reg key for those having similar issue.