After last weeks blog post about restricting which users can logon into a Windows 10 device, today another post about managing local users and local rights. In this post I show how we can create a local user account on a Windows 10 device with Microsoft Intune. Optional we can assign the local account Administrator rights.
Like in the previous post we need to use a Configuration Service Provider (CSP) policy and a Custom configuration profile to get the job done. This time we need to use the Accounts CSP.
All info we need can be found at the Microsoft docs here.
Configure the Custom Configuration profile
- Sign-in to the Endpoint Manager admin center
- Browse to Devices – Windows
- On the Configurations profiles tab click + Create profile
- Choose Windows 10 and later as Platform
- Choose Custom as Profile type
- Click Create
- Give the configuration profile a Name
- Enter a Description (optional)
- Click the Settings tab
- Click Add
A part of the OMA-URI contains the username for the local account we create: Users/{UserName}/LocalUserGroup
Replace UserName with the username of your choice. In my example I create a new user account with the username LocalUser.
The Data type is String.
As value we need to provide the password of the local user account.
In my example I create a local user account with the username LocalUser.
Enter below information to the policy;
Name: RestrictedGroups – ConfigureGroupMembership
OMA-URI: ./Device/Vendor/MSFT/Accounts/Users/LocalUser/Password
Data Type: String
Value: Your Password
Click OK.
Optional is the second Row we can add to assign the local user Administrator rights on the device. If this setting is not set, the user account will be a standard user account.
Click Add.
Enter below information to the policy if you want to assign Administrator rights;
Name: RestrictedGroups – ConfigureGroupMembership
OMA-URI: ./Device/Vendor/MSFT/Accounts/Users/LocalUser/LocalUserGroup
Data Type: Integer
Value: 2
Click OK (twice) and click Create.
Assign the profile to a security group and we`re ready to check the end result.
End result
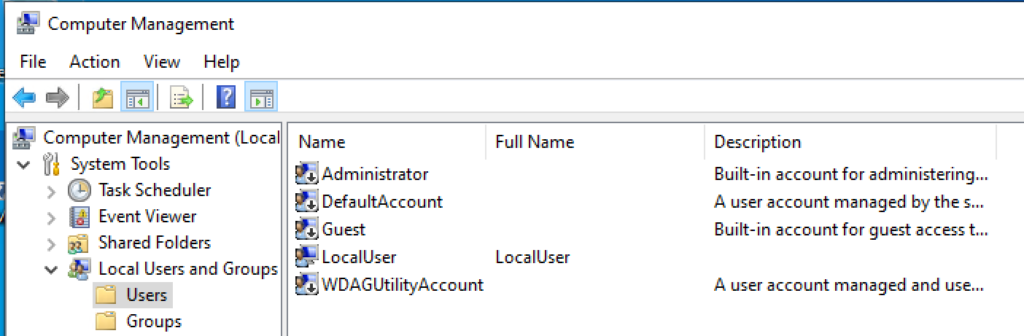
When we check the local Users via Computer Management, we see a new local user account is created. In this example LocalUser.
And I have added a second row to assign the new local user account Administrator rights. The local user account is member of the local Administrators group.
NB: If you want to sign-in with a local account into a Windows 10 Azure AD joined device, as with a AD joined device, put “.\” before the username.
That`s it for this post, thank you for reading!
NB: In the Endpoint Manager admin center, the policy shows an Error state even if the policy is applied successful.

34 Comments
hi
i think there is some mistake in your post
the 2nde one to assing local admin rights, i think the oma-uri is not good.
Also you said “replace UserName with the username of your choice. But on the oma-uri, it is “localuser” that we should replace right ?
Could you please be more specific ? or detail it more ? thanks 🙂
Hi Dan,
Thanks for pointing me on the wrong URL.
I hope the text is now more clear, if note please let me know. Than I will replace the text + screen shorts with a more clear example. I can imagine LocalUser as example isn`t very clear 🙂
thanks for the reply. By the way, great article, because, it works.
Just a tip : i would have put LocalUser (without S ! typo in your text 🙂 ) between brackets . This way, when we see the command line (the Oma-uri) we know that this text has to be changed.
Also, i would have mentioned that to login on a pc joined to AAD (with intune), you need to put “.\”. Without that, it will only accept AAD login, not a local one (at least on my computers…i don’t know if it is the common behavior).
Many thanks 🙂
Thanks for the feedback!
Yes you need to put “.\” before the username, like you need with an AD joined device.
Hi 🙂
It works but on intune it shows remediation failed. Dont know why…
But the policy is applied.
Same here, policy applied successfully only its keeps showing remediation failed.
Any idea why? or how to make it success @Peter
nevermind found this is still a issue.
Just want to check if this “remediation failed” is still showing up on your end? We’re trying to use the same steps and the deployment status always shows error -remediation failed. Thanks mate!
Hi guys!
I noticed the same, therefor the very first note of the article:
NB: In the Endpoint Manager admin center, the policy shows an Error state even if the policy is applied successful.
Seems that the GET part of the policy is not available in Windows and therefor Intune is not able to query the status of the setting.
Have seen that before with other policies, which was confirmed by MS the GET part was missing. So I guess that`s the same for this setting.
I had this issue when applying the policy to the user group because I was adding it to the user group, and the signed-in user was a standard account. Once I changed it to the dynamic device group the policy applied correctly.
Got the same thing, you can dig in the event logs (google the remediation error) does not give a lot to work on. But you are right, the new local admin/password is created. I tested on a few different machines and it’s the same error.
Sounds like Peter is on the right track. Thanks!
Hi Peter – This is awesome, thanks for the comprehensive post.
Is there a way to set the account password to never expire? I’m currently having isssues where when I create the local admin account, and I try to login/elevate, it forces me to update the password, and also it doesn’t check the box “Password never expire”
Thanks again
Hi,
I`m not aware of a possibility to set the password to never expires.
The account is targeted with the local password policy. You can target the machine wit a password policy, using a device restrictions profile, but there is no setting in that to set it to never expire.
Use the following in PS-script. Succesfully tested this:
Set-LocalUser -Name “ACCOUNT_NAME” -PasswordNeverExpires:$true
Hi Peter! This is terrific. One question for you…
Say you assign this policy to a device and the local admin account is created. Is it possible to reverse this policy and remove that account at a later date?
Appreciate your thoughts/knowledge. Thanks!
Use a powershell script and can push it out to machines you specify via security group.
February 2021: still getting the ‘Remediation failed’ error message…
Same here…. I created a script to run to add a local account, give admin rights and set the password not to expire but that also fails to run (both in device context and user context – the latter because the user isn’t an admin).
Hello All,
I created the Local account – LocalUser, with the same steps as mentioned. It worked fine with the Admin rights but when I tried to change the name of the account, it did not appear with Admin rights. What wrong am I doing? Can someone please guide me?
Hi Peter,
Thank you for the guide – I’ve been using this successfully for some time now.
As our requirements have now changed, for best practice I’d like to remove this account from all of our devices. How would I do this please?
I have just applied this policy (in a testing group) and waiting for it to replicate. I do have a question though that I hope someone can assist on. Does this only apply once? For example, our policies state that the local admin and guest accounts are disabled along with the the “backup” local admin account must have a unique password controlled by LAPS. Will this keep setting the password back to what is configured in the Intune Policy or does this only apply once so that LAPS can rotate the password every 30 days and store in AD?
I had configured the same in my infra, but after a few days, the account automatically gets removed from the Admin group even though I have specified the value”2″.
I get the same thing – it works, but have to run a sync every login for it to get into the admin group, not sure why this is happening.
How is the password passed through from/to computer and Intune? Clear text, encrypted? How?
Thanks.
Hi
It works fine when the HAADJ device is in Corporate LAN or though VPN. When syncing with Company Portal app from outside the localuser dows not appear. Is this expected?
please share troubleshooting steps or flow of policy on windows 10 machine I am getting error like currently looged user (i have logged to the machine as standard user) policy is not applied intune portal says error
Hi Peter, What is the recommended method to change the local account password? Changing this password in the same profile will not change the password if the account already exists. PowerShell is not recommended and should be avoid using plain text in scripts or from command line.
Please let me know what your recommendation is 🙂
Since this comment then have added Cloud LAPS. Works quite well. As long the user account has been created.
I am unable to get this configuration policy to apply successfully in any manner
it shows setting status of Error, error code 0x87d1fde8
Any help would be greatly appreciated
Thank you,
Getting the same 0x87d1fde8 error. Wondering if this is affected by default security policies.
Helo , that work for updating password for existing account ?
This is outdated in 2023
You will get remediation errors and you have to run an additional script to set the password to “never expires”, but besides that it’s still working on current W11 build.
Why is this outdated? If there is a better method to create a local account on a device and add it to a specific group without using powershell remediation scripts, please share.