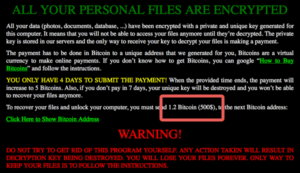
 Ransomware is shaping up to be the most important threat from the hacker community this year. Ransomware is malware, often received via a malicious email, which encrypts your files and making them inaccessible by for example opening the email attachment you thought it was an invoice from one of your suppliers. To decrypt your files you have to pay an amount of money to the hacker, usually by bitcoins.
Ransomware is shaping up to be the most important threat from the hacker community this year. Ransomware is malware, often received via a malicious email, which encrypts your files and making them inaccessible by for example opening the email attachment you thought it was an invoice from one of your suppliers. To decrypt your files you have to pay an amount of money to the hacker, usually by bitcoins.
After paying the amount of money it is not guaranteed your files will be decrypted. So you have to restore your files from backup (I hope you do have a good backup solution) or use previous versions when using a Windows file share or SharePoint library (but I have seen examples of ransomware which encrypted the previous versions as well). What ever solution you have to restore your data file, it will cost you and your company a lot of time and money to get access to your files.
You try hard to avoid a situation being infected by ransomware, viruses etc. by running an anti-virus solution to scan inbound email and running anti-virus software on the users computers. You instruct employees not to open malicious emails, but one moment of not paying attention and an employee may activate ransomware on your network. Known ransomware will be noticed and deleted by the anti-virus software, but zero-day exploits won`t and may cause a lot of damage on your network. Microsoft provides a great solution against these zero-day exploits received via email with Exchange Online Advanced Threat Protection.
Exchange Online Advanced Threat Protection (ATP) provides users additional protection against specific types of advanced threats. ATP will protect against unsafe attachments even if their signatures are unknown with Safe Attachments. 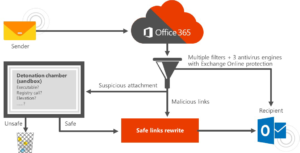 All suspicious content goes through a real-time behavioral malware analysis that uses machine learning techniques to evaluate the content. Unsafe attachments are sandboxed in a detonation chamber before being send to the recipient.
All suspicious content goes through a real-time behavioral malware analysis that uses machine learning techniques to evaluate the content. Unsafe attachments are sandboxed in a detonation chamber before being send to the recipient.
But ATP will not only protect the emails against malicious attachments, it will also protect against malicious links in your emails. Safe Links examines the url`s and rewrites the url`s. At the time a user clicks on an unsafe url he is warned not to visit the site or the site is blocked. This real-time scan of the url is done every time the url is clicked on, so you will be protected even if the destination of the url is changed since receiving the email.
For you as an administrator you get rich reporting tools as part of ATP to get insights into who is being targeted in your organization.
Exchange Online Advanced Threat Protection is available for every company who uses Exchange Online Protection (EOP) to filter inbound email. Office 365 users are using EOP by default and on-premises can also purchase EOP and ATP for scanning their inbound email.
If you are interested how ATP works, watch this video in which Shobhit Sahay and Jeremy Chapman show you the capabilities of ATP in more depth.

I visit day-to-day a few web pages and websites
to read posts, however this blog gives quality based articles.